Yesterday my publisher told me that she emailed a ticket to Amazon Central to fix my Amazon page and got back to them three times, but no one got back to her, over two weeks. Amazon Central is very good about getting back to writers--and even better at getting back to publishers. My publisher believed this was unusual, too.
Since I know Greg views and deletes my emails--and gets into my associates' emails and deletes those too sometimes--I suspect Greg killed my publisher's emails to Amazon. After all, he has a strong motive to limit the publication of a book that exposes him. I believe he removed my Amazon page for this reason, and it's certain he will employ his hacking skills to harm the reach of The Lord's Hacker. He has earned my title for him--the censorship publisher.
I'm sure he's been all around my publisher's offices, getting his peeks at pretty women, taking down his pants and whispering misogynistic words through shut teeth (as Pope Innocent III watches from his picture frame) and also checking out where my book is on their lists while he enjoys a creme-filled donut.
People's past selves give insight into their currents selves especially when they're not interested in changing.
But after thinking about it some more, I don't buy it. For one thing, I'm not a big author. People aren't typing my name into Amazon enough times to change algorithms at the biggest online company in the world.
Also, Gregory Wolfe is a vicious, skilled hacker who wants me to see that he can change addresses on police forms and publishing submissions, who placed his face on my blog, took this post about him offline, deleted all of my followers, and disabled comments. He has hacked members on my email shoutout list because he believed they were getting too close to me. He has vacated almost all of my blog posts from Google listings. He hacked the CEO of Wipf & Stock to force removal (unsuccessfully) of Horses All Over Hell. He shut down my Facebook and prevented my creating an X account, deleted my emailed book submissions, created spelling and grammar errors in story manuscripts, held onto control of my Google panel, dropped most of my prestigious content from top Google pages, and placed my one negative review front and center. He has threatened me with death images and repeated pictures of my son sent via Messenger.
It's not a stretch to imagine that he found an app on the dark webs that could type the name "Blackett" into the Amazon system thousands of times to where the algorithm changed my name--or he could simply remove the page. At any rate, I believe he did something like that. And this was an act of hacking he wouldn't want to be seen, because it would amount to a serious act of censorship. The beauty of it is that the Amazon algorithm really does change names from time to time. He has cover there. The problem is that he's an ardent, daily hacker, so this potential glitch deserves much greater scrutiny and suspicion than it normally would.
In 2020, I mentioned to my email shoutout group that he had gotten into my Xfinity account and made it almost impossible to complete the set up. When I tried to contact support, I got Gregory Wolfe on the texts! He wrote many silly, lighthearted things, like "Oops, sorry!" And he has done this a few other times at other apartments. I have mentioned that he pretended to be my son on Digital Touch. He has blocked countless calls I've tried to make on my phone, just to be an ass. He has created false waiting music for my calls to my doctor that are not in fact the music my doctor's office plays in its phone que. He can get into any system and sneak undercover. He is the very champion of dark web apps.
Gregory Wolfe has the skills and the fierce, constant obsession and sense of self-protection to seek to do whatever it takes. I don't believe for a second it was a glitch that my Amazon author page vanished one month after God's Hacker was accepted for publication. "Oops, sorry!" I do not believe it.
Background: Judge Charles Carlson
Highlights
Enemy Email
Illegal Porn
My Hacker Fired for Sexual Harassment
My Hacker is Known for his Dick Pics
Ashley Madison and "The Evil Dead"
These screen shots were deleted from my phone. It's lucky that I had posted them in a private Facebook post.
Manipulates Dating Site
In May 2019 I dated a black woman through a website in Cincinnati when I was divorced. She was a Christian and wanted me to be one, and it didn't work out. In a few weeks, I looked at the dating site again and saw it was all very large black women who were looking only for sex, at least that was all I could see on the site. He seemed to say, Oh you want a black girl? Try one of these.
Sends Infected emails to My Student
Hacks Colleagues and Editors

Spoofs Dick Pics to my Date
Another Editor Hacked
Psyops Noises Issue from My Computer
Hospital Stay
Swaps Digital Info on Caller ID
In November 2023 my hacker switched the name of my doctor and my pest control in my phone's address book, to suggest that I needed to be treated like a pest. He often switches caller ID so I don't know who is calling. My digital world is so full of glitches, I don't believe in glitches anymore.Friend Requests From Kids
Blocks My Phone Calls etc.
Sometimes I can call my doctor's office, but it rings and rings. Or a robot answers and puts me in a cue, but it's not the standard music that my doctor's office plays, and no one ever picks up.
Spoofs My Landlord and Tries to Get Me Kicked out of My House
At the very least, my hacker is certainly not being careful right now. His brand has tanked, and he blames me instead of his behaviors. He's doing things, with greater repetition, that he wouldn't have done last year.
It was Wolfe, pretending to be my son! Yes, things are getting weird. No surprise, he deleted this digital touch exchange, and deleted the screenshot of it later.
Suicide Included in My “Friends”

Constant Social Media Censorship
In November 2023 I joined the Facebook page Beat Poems On the Road and was receiving 500 to 900 likes on my posts. The admin, Steff, got hacked and cut me off. In Facebook pages I frequent, my hacker often uses an avatar to bark at me and complain to the admin about me. If this doesn't work, he hacks them until they drop me. I have experienced this five or six times. In the case of Beat Poems, I believe he couldn't handle that I was getting so much exposure, and he had to put an end to it.
One judge, in 2021, told me, when I mentioned my hacker's porn harassment online, "That's his free speech!"
There is something wrong with our laws on cyber harassment right now. We can't seem to locate a sensible position on the issue. When we police speech online, we tend to target political speech, so we correct that overreach by backing off and allowing ghastly crimes to go unchecked.
If someone sends you death images and porn and then twenty pictures of your son or daughter from your iphone memories, in meaningful and threatening repetition, not even the fiercest Libertarian would say, "Free speech! I love this!"
But I was pleased to hear this judge agreed that his behavior may well be psychotic and dangerous and that the internet is a running ground for criminals. At least she didn't pretend that all is well and that it's free speech.
Questions
I wanted to address any who might believe I have no evidence, simply because I lack an IP or a photograph of my hacker caught in the act. As Judge Charles Carlson told me at the hearing, I have evidence that would be persuasive in civil court, and my assertions raise many questions that point directly to Gregory Wolfe.
For instance, who placed Greg's picture on my blog for two weeks, a threatening gesture, after my post went live? Only my hacker would place his image on my blog.
Who removed the many followers of this blog before I posted "A Christian Leader's Life"? Some other nemesis?
Who deleted the emails from my hacker to me and then restored some of them but not all? Who else had a motive?
Who deleted my email containing the porn descriptions that my hacker used to cover my Google pages, the email I had sent to the scholars? Who else would want to?
Who edited "A Christian Leader's Life" a few times after it went live, to convey a frivolous and unedited and sometimes confusing vibe so that I had to keeping rewriting it?
Who replaced the screenshot of the fake email that contained the iPhone memory?
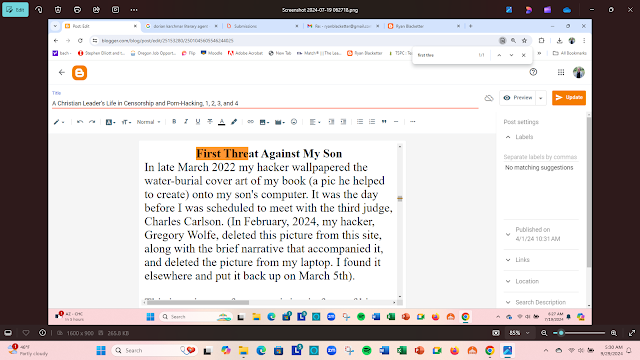
Who deleted the photo I took of my son sitting in front of his computer? It was wallpapered with my book cover art that my hacker had helped create. My hacker had the motive.
Who is so focused on my son that he has to keep sending me his pictures to convey a threat? Who else deletes his texts? Some other random hacker?
Who demeaned, repeatedly, working class people in fake blogs and on my blog, just as he demeaned the working class background of one of the women who fired him?
Who else would spoof my police report about my hacker, placing my landlord’s name and email and phone on the report?
What else would be interested in my communication about my hacker to the police?
If it was a different hacker, he must have been very sympathetic to Gregory Wolfe and spent a lot of time covering for him and concealing his crimes.
"Change your passwords." This is advice I've heard from tech people, many who make a lot of money. This advice is also a favorite of cops. Even IT "experts" will tell you that you need to change passwords often. You should change them to guard against low-level types. But advanced hackers use a technique called "forced entry" to bypass passwords. I remember when I was in Pittsburgh I was changing my passwords all the time, and that never worked. Greg may have some program that captures password changes. But don't forget, Russian and Chinese hackers have recently blasted their way into Pentagon computers, despite the most advanced defenses in the world, and owned them at every level. A really good hacker can certainly get into my computer and yours.
At any rate, yes, he gets into Gmail, Facebook, Blogger, LinkedIn--all of the apps.
Regarding his ability to reorder Google content, one person told me years ago, "I doubt he has access." Again, hackers hack. They don't ask for passwords or dig them out of your trash. I have documented that many items rise and fall rapidly on my Google pages. Greg even wallpapered my Google pages with porn descriptions--In 2019 I Googled my name and there they were (see below)--and it took three days for the junk to clear out.
There's a lot of innocence about hacking. But things are changing. More people know what spoofing is now, for instance. The FBI knows that a spoofer owns your phone and can send your pictures of your naked body to your husband's friend, so it looks like you're sending it to flirt. And the FBI no longer says corny, low-level stuff like, "Did you change your passwords?"
If an IT dude who seems smart about defending your computer but has no experience dealing with an advanced hacker--if he tells you "nobody's getting in" and "change your passwords," I hope you'll be a bit skeptical. Be skeptical of me too, but at least I have had some experience with a master hacker, and I've shown fifty-plus pages of real-life hacks. It's true some of it is just based on my word. But most of it is based on alarming screenshots and narrative of my experience.
I don't wish to dismiss all IT people, only to say that most of them aren't ready to defend the Pentagon. But one IT guy I met actually had a lot of experience with hackers. He worked with a lawyer I employed last year. He was familiar with top-drawer hacking. When he looked at my GW post, he said it was obvious that I'm the victim of a crime. The lawyer said the same thing, but they asked for money I didn't have beyond the $700 I had already handed out.
Places Face on My Blog as Warning
March 20, 2024. Greg placed his face on my blog after I posted "A Christian Leader's Life." My blog has always used the picture on the top post for the site picture (after two or three days), no matter how popular a post below it might be. This Moses pic was on my blog for two weeks.
Deleted Blog Followers
Eugene Weekly
March 27, 2024. After I posted "A Christian Leader's Life," the Eugene Weekly editor said she wanted to do an investigative article on Wolfe. When I called days later, I found a generic, robot voicemail and left a brief message. Later in the day it struck me as odd that the voicemail would be generic. He has placed fake voice systems on my phone before.
I left my house, getting away from Wi-Fi, and called again, down the block. This time there was a real voice thanking the caller for contacting Eugene Weekly, but it was closed so I left no message.
Greg has intercepted many of my calls, often just to be a creep, but sometimes to keep me from talking to someone he doesn't want me to talk to.
Eugene Weekly
Froze My Site Visit Counter
June 22, 2024. Right after I posted this today, I saw thirty people visited the site right away. Then the counter was turned off. That's Greg's way of staying in charge--again with the censorship. He also turned off my visit counter when I posted the two paragraphs from Poets & Writers last week. He doesn't believe anyone should get notice that's a little better than what he has. He's also angry about that post because he doesn't want to explain why I dumped Slant, especially since he pretended that it was his idea that I left--awkward! [The counter resumed six hours after this post went live].
When I blocked one young prostitute, my screen froze on my phone, but I was able to block the rest on my computer.

June 28, 2024. Greg deleted this polar bear photo from this site and from my desktop today, and I took another screenshot of it. He has deleted other photos related to his harassment concerning my son, as described elsewhere in this document, possibly because he doesn't think that obsessing about someone else's child is a very good look. He would be right.
Some radicals say that Christians are often perverts. It’s more accurate to say that perverts are often Christians. They need an identity behind which to hide. Most perverts understand they can’t live in society as the way they are. Some become Christian leaders. Christian author M. Scott Peck explores this phenomenon in People of the Lie.
This morning when I opened my phone I found that an off-white “card” had been placed over most of the text of our emails. Last year, Gregory Wolfe sometimes placed such cards on the very Word doc of The Lord's Hacker as I was writing it. He never left it there for more than a minute. He was just using one of his myriad hacking tricks and wanted to send the message that he’s in charge.
This time I believe Greg's covering up my emails with the editor communicates that he’s going to cancel my arrangement with the editor, that he’ll ruin it somehow, as he always does.
Greg’s censorship is tricky in several ways. Not only has Greg sent infected emails to publishers in my name—and will likely do so again—but there’s also the psychology of the publisher to consider. Though most publishers find censorship despicable, they also don’t want to walk into controversy or open themselves up to attack by malevolent actors.
It’s easy to look back at beloved writers who were censored and wonder why they were so alone in their fight, like Isaac Babel and Rousseau.
It’s only later, usually after the censored author and his enemies are dead, that supporters seek to publish their censored work. I don’t place myself in that company of luminaries—nor do I see most rejections as censorship—but I do expect fearful silence and cold shoulders from any publisher who learns of the hacking. That’s what Gregory Wolfe wants too. He loves to see his terror result in destroyed relationships and neglected books. He’d burn them if he could. Being a publisher must offer psychological cover for this passion he has for censorship.
All Greg has left is the ability to frighten people. When Orwell imagined the future as a boot stomping on a human face, he surely conjured tyrants like Gregory Wolfe. I hope there are some, like the fighters in the French Resistance, who are willing to take some risks against a true enemy of humankind.
.jpg)









.jpg)












.png)
.png)
































No comments:
Post a Comment